This past spring, as the COVID-19 pandemic took hold, online learning became the new norm as universities and classrooms around the world were forced to close their doors. By April 29, 2020, more than 1.2 billion children across 186 countries were impacted by school closures.
Shortly after schools began to transition to emergency remote learning, it became clear that many were not ready for the kind of full-time, digital education now needed. Not all students had the technology that was required, from laptops to a stable Internet connection, and parents and instructors in countries like the United States worried students would inevitably fall behind academically. What is more, many educational institutions did not have proper cybersecurity measures in place, putting online classrooms at increased risks of cyberattacks.
In fact, in June, Microsoft Security Intelligence reported that the education industry accounted for 61 percent of the 7.7 million malware encounters experienced by enterprises in the previous 30 days – more than any other sector.
Apart from malware, educational institutions were also at increased risk of data breaches and violations of student privacy. It was this spring that “Zoombombing” became part of the general lexicon after pranksters and ill-intentioned individuals began taking advantage of Zoom’s security weaknesses to break into private meetings. Among the victims were schools, with several reported incidents of online classrooms being interrupted by users making lewd comments or streaming pornography.
As fall approaches, digital learning will continue to be a necessity. In fact, half of all U.S. elementary and high school students will be entirely online. Even those that are reopening are deploying some kind of hybrid model, such as delivering large lectures online. What’s more, the threat of a second coronavirus wave still remains, meaning that future large-scale school closures are still a possibility.
With this in mind, Kaspersky researchers took a closer look at the cyber risks faced by schools and universities, so that educators can be prepared moving forward – and take the necessary precautions to stay secure.
Methodology
This report examines several different types of threats – phishing pages and emails related to online learning platforms and video conferencing applications, threats disguised under the names of these same applications, and distributed denial of service (DDoS) attacks affecting the education industry.
Various threats disguised under popular online learning platforms/video conferencing applications
For this part, we utilized results from the Kaspersky Security Network (KSN) – a system for processing anonymous data related to cybersecurity threats shared voluntarily from Kaspersky users – for two different periods: January-June 2019 and January-June 2020.
Using KSN, we searched for files bundled with various threats that contained the name of one of the following platforms/applications during one of the two periods above:
- Moodle – the most popular learning management system (LMS) in the world. It is used by educators to build online courses, host classes and create activities.
- Blackboard – another popular LMS. It provides a virtual learning environment where educators can build entirely digital courses or create additional activities to supplement in-person instruction.
- Zoom – a highly popular online collaboration tool that provides free video conferencing capabilities. Many educators used Zoom to conduct online classes this past spring.
- Google Classroom – a web service designed specifically for educators to host classes, generate assignments and track students’ progress.
- Coursera – a popular online learning platform that hosts a variety of open online courses, certificates and even degree programs.
- edX – a provider of open online courses available to users worldwide.
- Google Meet – a video communication service similar to Zoom, which can be used to host meetings and online classes
The results display those (PC and mobile) users that encountered various threats disguised as the above platforms/applications from January-June 2019 and January-June 2020.
Distributed denial of service (DDoS) attacks
Kaspersky tracks DDoS (distributed denial of service) attacks using the Kaspersky DDoS Intelligence System. A part of Kaspersky DDoS Protection, the system intercepts and analyzes commands received by bots from C&C servers. The system is proactive, not reactive, meaning that it does not wait for the user device to get infected or a command to be executed. Each “unique target” represents a specific IP address that was attacked.
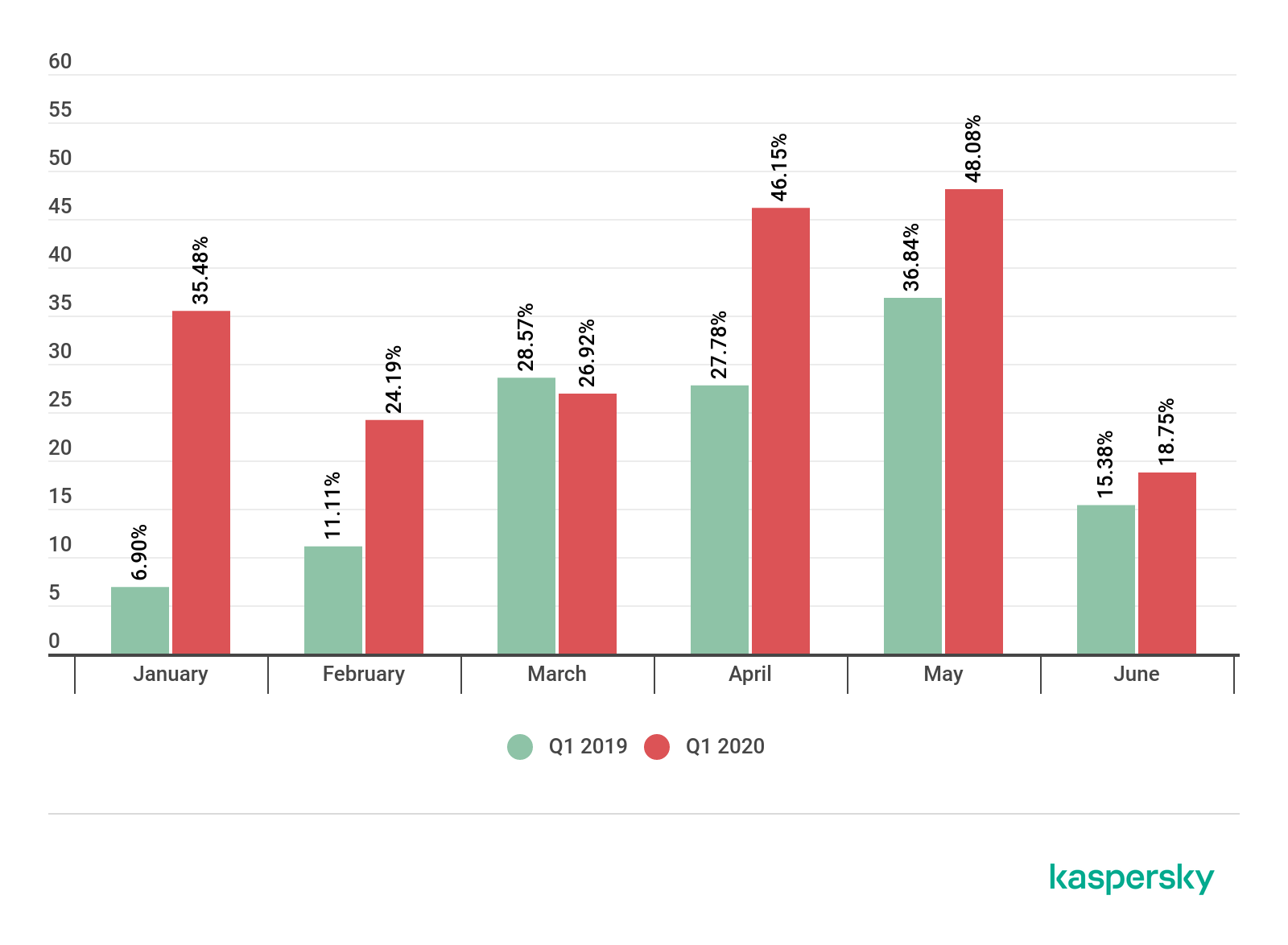
The following report displays the percentage of DDoS attacks that affected educational resources out of the total number of DDoS attacks registered by the Kaspersky DDoS Intelligence System for Q1 2019 and Q1 2020.
- Our Key Findings. The number of DDoS attacks affecting educational resources grew by 550% in January 2020 when compared to January 2019.
- For each month from February to June, the number of DDoS attacks that affected educational resources out of the total number of attacks was 350-500% greater in 2020 than in the corresponding month in 2019.
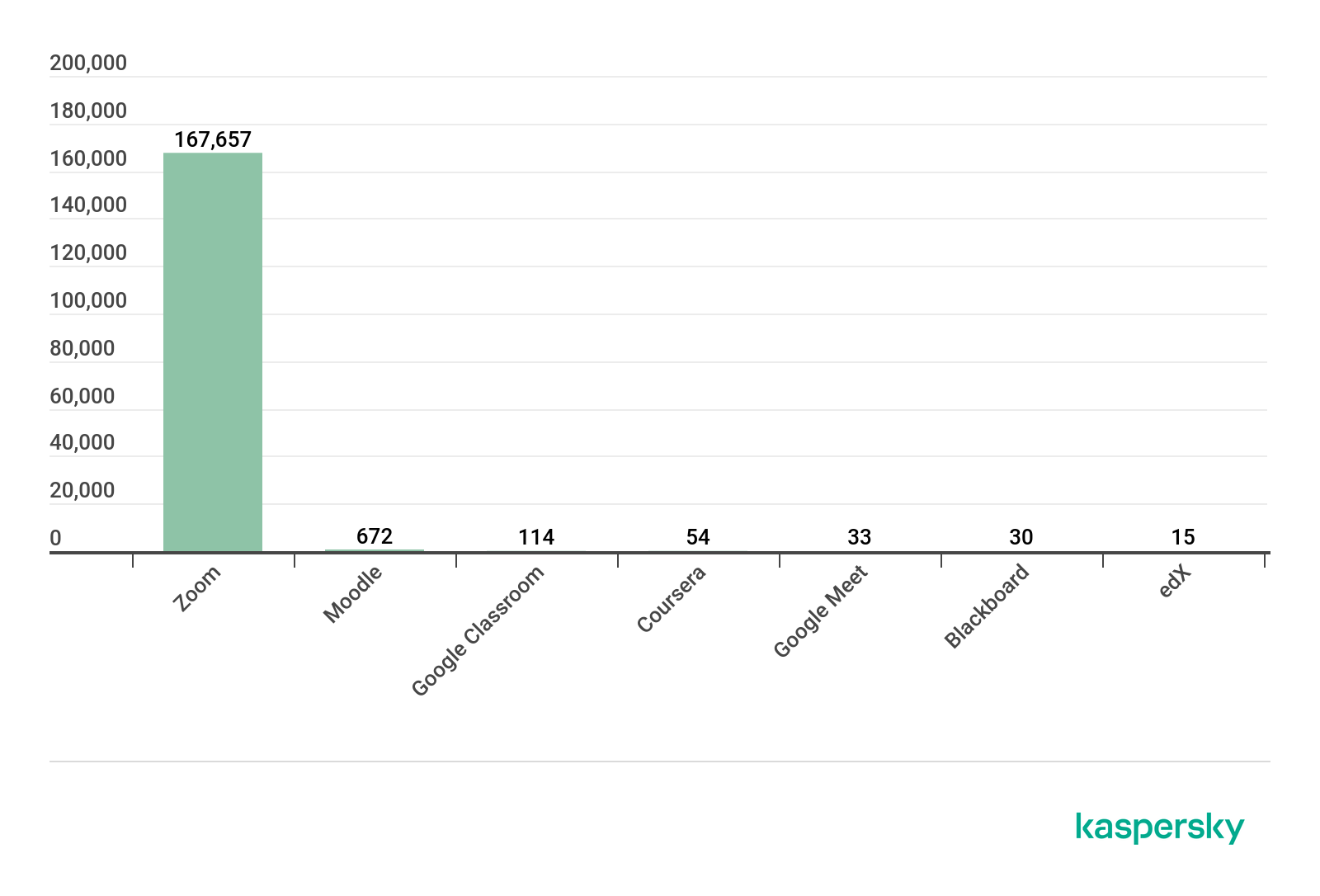
- From January to June 2020, the total number of unique users that encountered various threats distributed under the guise of popular online learning platforms/video conferencing applications was 168,550 – a 20,455% increase when compared to the same period for 2019.
- From January to June 2020, the platform most commonly used as a lure was Zoom, with 5% of the users that encountered various threats encountering them via files that contained the name Zoom. The second most common platform used as a lure was Moodle.
- By far the most common threats encountered in 2020 were downloaders and adware, which were encountered in 98.77% of the total registered infection attempts. Various classes of trojans followed adware.
- For threats distributed under the guise of popular platforms for conducting online classes in 2020, the highest infection rate was registered in Russia (59 attempts per 1000 users) followed by Germany (39 infection attempts per 1000 users).
Phishing risks of online learning platforms / video conferencing applications
It is not unexpected that phishing, one of the oldest and most popular forms of cybercrime, would reach educational organizations. In fact, a host of phishing websites for popular platforms like Google Classroom and Zoom began to pop up following the switch to distance learning. From the end of April to mid-June, Check Point Research discovered that 2,449 domains related to Zoom had been registered, 32 of which were malicious and 320 were “suspicious”. Suspicious domains were also registered for Microsoft Teams and Google Meet. Users who land on these phishing pages are often tricked into clicking URLs that download malicious programs, or they might be tricked into inputting their login credentials, which would put these in the hands of the cybercriminals.
Fake login page for Zoom
Fake login page for Moodle
These criminals might not even be after access to your account. They can use your login credentials for various nefarious purposes: launching spam or phishing attacks, gaining access to your other accounts as people often reuse passwords, or collecting more personally identifiable information to be used in future attacks / attempts to steal funds.
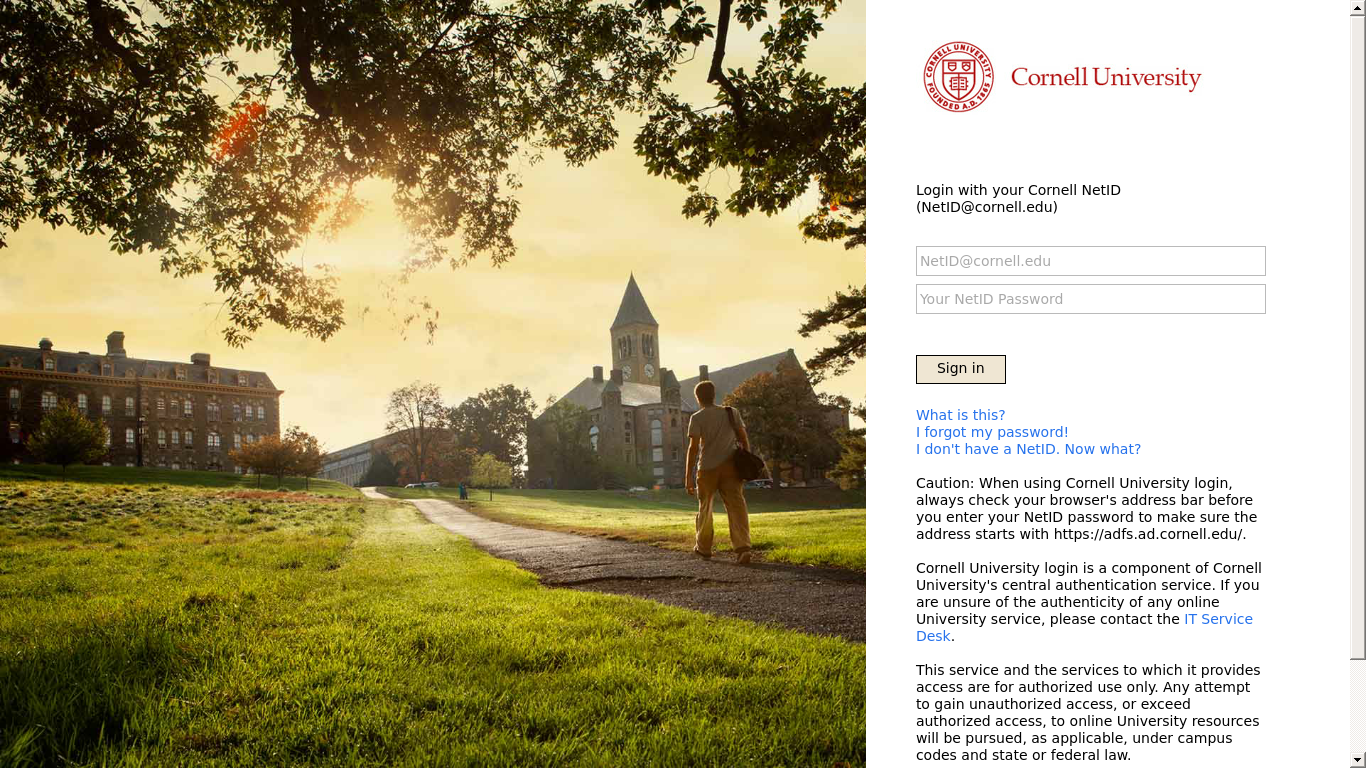
Most universities also have their own platforms where students and faculty can login to access important resources and various academic services. This past spring, some attackers went so far as to target specific universities by creating phishing pages for their individual academic login pages.
Phishing page for Cornell University’s academic login page
Apart from fake web pages, cybercriminals sent out an increasing number of phishing emails related to these same platforms. These told users they had missed a meeting, a class had been canceled, or it was time to activate their accounts. Of course, if they opened the email and clicked on any links, they were at risk of downloading various threats.
Phishing email supposedly from Zoom urging the user to review a new video conferencing invitation
The cyberthreats of online learning platforms
A common way to distribute threats disguised as popular video meeting apps and online course platforms is by bundling threats as legitimate application installers.
There are several ways users can encounter these malicious installers. One way is through phishing websites designed to look like the legitimate platforms, as seen above. Those users who inadvertently end up on the wrong page are then exposed to malware or adware when they attempt to download what they believe is the genuine application. Another common way is through phishing emails disguised as special offers or notifications from the platform. If users click the links in the email, then they are at risk of downloading unwanted files.
From January to June 2019, the number of unique users that encountered various threats distributed via the platforms specified in the methodology section of this report was 820.
The number of unique users that encountered various threats disguised as popular online learning/video conferencing platforms, January – June 2019 (download)
The most popular lure was Moodle, with Blackboard and Zoom being the second most popular.
In 2020, however, the total number of users that encountered various threats disguised as popular online learning platforms jumped to 168,550, a 20,455% increase.
The number of unique users that encountered various threats disguised as popular online learning/video conferencing platforms, January – June 2020 (download)
Zoom was far and away the platform most frequently used as a lure, with 99.5% of users encountering various threats disguised under its name. This is not surprising given that Zoom became the go-to video conferencing platform. By February 2020, the platform had added more new users (2.22 million) than it had, in all of 2019 (1.99 million). As of April 30, the company claimed to have 300 million daily meeting participants. Given its immense popularity, it is only logical that it would be the preferred target for malicious actors. And, with millions of more users looking to download the application, the chances are high that at least some of these would come across fake installers or setup files.
A closer look at the 2020 threat landscape
Types of threats encountered
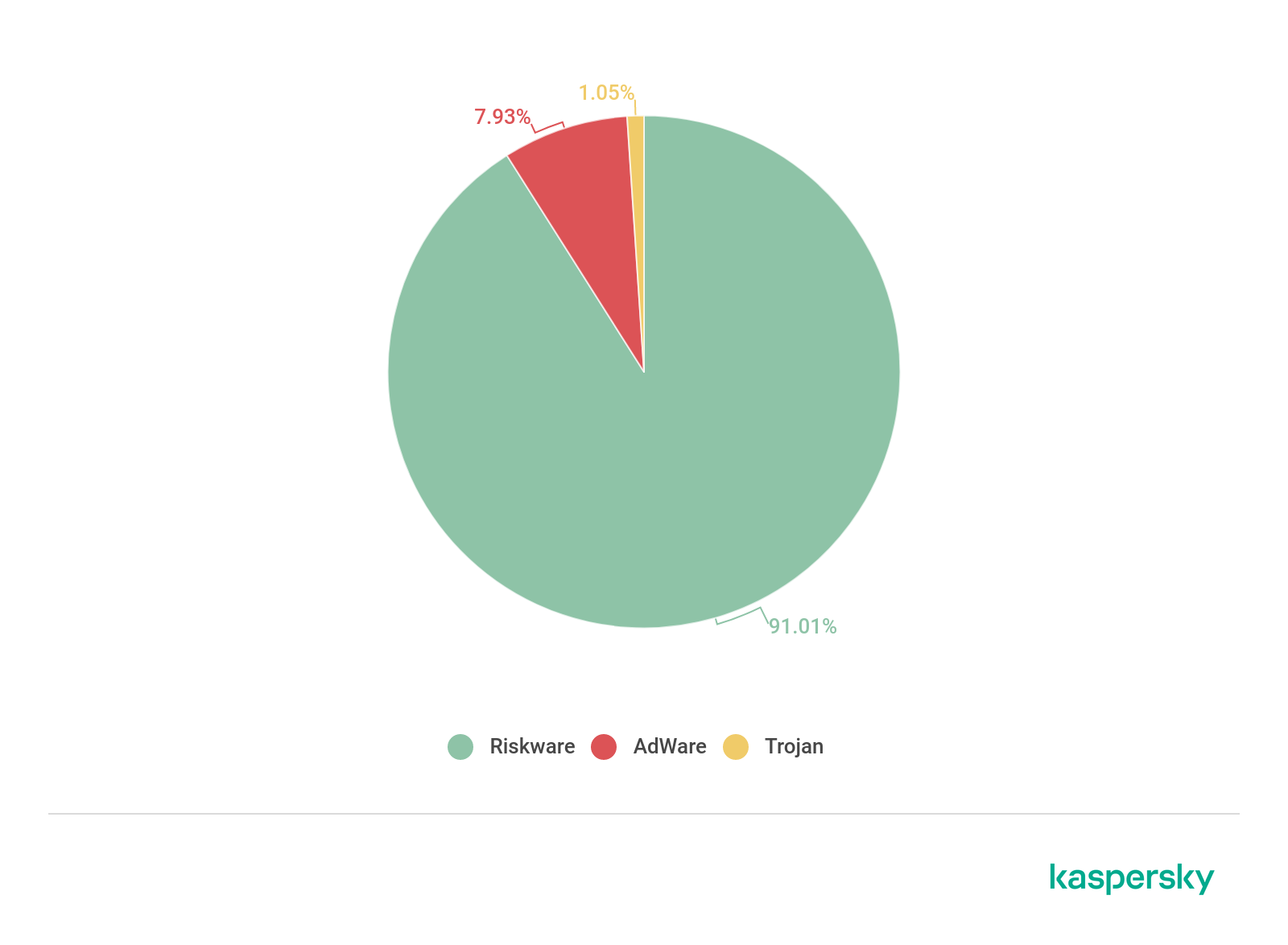
Percent distribution of different types of threats disguised as popular online learning / video conferencing platforms encountered by users, January – June 2020 (download)
By far the most common threats distributed under the guise of legitimate video conferencing/online learning platforms were not-a-virus (99%). Not-a-virus files are typically divided into two categories: riskware and adware. Adware bombards users with unwanted ads, while riskware consists of various files – from browser bars and download managers to remote administration tools – that may carry out various actions on your computer without your consent.
About 1% of the infection attempts were various trojan families: malicious files that allow cybercriminals to do everything from deleting and blocking data to interrupting the performance of the computer. Some trojans encountered were password stealers, which are designed to steal your credentials, while others were droppers and downloaders, both of which can deliver further malicious programs on your device.
Other threats encountered were backdoors, which allow the attackers to take remote control over the device and perform any number of tasks; exploits, which take advantage of a vulnerability in an operating system or application to gain unauthorized access to/use of the latter; and DangerousObjects (non-specific malicious files).
A regional perspective
The five countries with the highest infection rate are as follows:
| Russia | 59 infection/1000 users |
| Germany | 39 infection attempts/1000 users |
| Austria | 27 infection attempts/1000 users |
| Isle of Man | 13 infection attempts/1000 users |
| Switzerland | 10 infection attempts/1000 users |
came from Germany (39 infection attempts/1000 users%). Both countries closed schools early in mid-March, making remote learning the only option for millions of teachers and students. In addition, video conferencing has become incredibly popular in Germany, with more than half of Germans regularly using it as a tool for work or school. Given the overall global popularity of Zoom, a significant portion of Germans most likely use this platform and – given that Zoom is by far the most popular platform used as a lure – encountered various threats as a result.
Educational resources hit by DDoS attacks
In April, a large Turkish university was forced entirely offline for 40 minutes after it was hit with a DDoS attack on the morning of exams. In June, a major university in the northeastern United States had its exams disrupted after a DDoS attack affected its online test platforms. These are just two examples of a larger trend that began after schools were forced to transition to emergency remote learning: the rise of DDoS attacks against the education sector.
In general, the total number of DDoS attacks increased globally by 80% for Q1 2020 when compared to Q1 2019. And a large portion of that increase can be attributed to the growing number of attacks against distance e-learning services.
Percent of the total number of DDoS attacks that affected educational resources: Q1 2019 vs Q1 2020 (download)
When compared to Q1 2019, the percentage of DDoS attacks affecting educational resources out of all DDoS attacks increased steadily for each month of Q2 2020 (with the exception of March). When looking at the total number of DDoS attacks that occurred between January and June 2020, the number of DDoS attacks affecting educational resources increased by at least 350% when compared to the corresponding month in 2019.
| January: | February: | March: | April: | May: | June: |
| 550% | 500% | 350% | 480% | 357.14% | 450% |
The percent growth in the number of attacks on educational resources when compared to the same month in 2019
The more educational organizations rely on online resources to conduct their regular activities, the more of a target these networks become for cybercriminals looking to disrupt their operations.
Looking forward
Online learning is not a short-term response to a global pandemic. It is here to stay.
For one, the pandemic is not over. Many students are still studying virtually, at least part of the time, and some schools that decided to open have already decided to revert back to online classes only. The possibility of a second wave still looms, meaning educators have to be prepared for large-scale school closures in the future.
Even when the pandemic does end, most agree that online learning will not disappear altogether. A recent global survey by Pearson Education, an academic publishing company, found that nearly 90% of the 7,000 individuals surveyed expect online learning to continue to play a role at all education levels.
In fact, even before the pandemic, some universities had already developed blending curricula (a mix of offline experiences and online courses). More and more academic institutions are considering this as an option for future programs.
However, as long as online learning continues to grow in popularity, cybercriminals will attempt to exploit this fact for their own gain. That means educational organizations will continue to face a growing number of cyber risks – into this fall and beyond. Fortunately, engaging – and secure – online academic experiences are possible. Educational institutions just need to review their cybersecurity programs and adopt appropriate measures to better secure their online learning environments and resources.
The extended version of the report with security tips and additional materials from our partners: llya Zalessky, head of educational services at Yandex, Steven Furnell, professor of cyber security at the University of Nottingham, and Dr. Michael Littger, executive director of Deutschland sicher im Netz e.V, can be downloaded in PDF format.






















Digital Education: The cyberrisks of the online classroom