
News overview
Not just one but two new DDoS amplification methods were discovered last quarter. In mid-May, Israeli researchers reported a new DNS server vulnerability that lurks in the DNS delegation process. The vulnerability exploitation scheme was dubbed “NXNSAttack”. The hacker sends to a legitimate recursive DNS server a request to several subdomains within the authoritative zone of its own malicious DNS server. In response, the malicious server delegates the request to a large number of fake NS servers within the target domain without specifying their IP addresses. As a result, the legitimate DNS server queries all of the suggested subdomains, which leads to traffic growing 1620 times. A new version of DNS server software fixes the vulnerability.
About a week later, Chinese researchers posted information about another DDoS amplification method, named RangeAmp. The method exploits HTTP range requests that allow downloading files in parts. The experts found that a malicious range request can make content delivery networks (CDNs) increase load on a target site several times. The researchers identify two types of RangeAmp attacks. The first involves sending traffic from the CDN server directly to the servers of the target resource while amplifying it 724 to 43330 times. In the other case, increased volumes of garbage traffic are transferred between two CDN servers, with the amplification factor reaching 7500. According to the researchers, most CDN providers have released updates that safeguard their servers from this kind of attack or have stated an intention to do so.
As researchers investigate these new ways of amplifying attacks, DDoS botnet owners look for new resources to expand them. In June, our colleagues at Trend Micro discovered that the Kaiji and XORDDoS malicious programs, which formerly specialized in IoT devices, were targeting unprotected Docker servers. In the event of a successful attack, a XORDDoS bot penetrated every container on the server, and Kaiji created one of its own. Docker containers may prove unsuited for DDoS attacks — in particular because of the possibility of limiting the number of network protocols they use. Therefore, unprotected containers are attacked primarily by mining bots. However, some malware successfully combines a DDoS bot and a miner. For example, a bot that can both stage TCP, UDP and HHTP DDoS attacks, and hijack cryptocurrency for its operators was recently discovered in the wild.
The resonant socio-political events that marked the first quarter of 2020 could not but alter the picture of DDoS attacks. Thus, attacks on human rights organizations in the United States soared 1,120 times at the end of May. This activity coincided with the protests that unfolded in that country. The opposite side of the conflict was affected, too: the Minnesota State Information Technology Services were targeted by a DDoS attack. In particular, unknown hackers knocked out the Minneapolis police website. Around the same time, several tweets alleged that Anonymous hacktivists, who had previously threatened to expose police crimes, were behind the attack, but the group did not claim responsibility for the incident.
In June, Russia hosted a multi-day vote on amendments to its constitution, and preparations for the event were marked by DDoS attacks. The day after the voting began, the Central Election Commission said it had been attacked. The online voting service was hit right after the CEC, but officials said its operation was not disrupted. The service was experiencing outages at the beginning of the voting process: it could not handle legitimate load. The конституция2020.рф information website (covering the amendments into the RF constitution) was attacked as well. According to a CEC spokesperson, the site was inundated by garbage traffic originating in Great Britain and Singapore on June 28.
The media traditionally received their share of the attacks. This time, the Belarus Partisan independent social and political publication came under attack. According to a spokeswoman, the portal was flooded from foreign IP addresses before sources located in Belarus joined in. The owners of the website were forced to change its IP address. Belarusian online media have increasingly been targeted by DDoS operators.
The second quarter of the year in many countries saw measures to fight the COVID-19 pandemic, with the employees of many countries and institutions working remotely as before. Accordingly, the number of attacks on online resources remained high. According to Russia’s Rostelecom, the number of attempts at knocking offline education websites, such as e-diaries, instructional platforms, testing sites, etc., grew more than five times.
However, not every large-scale communication outage is a consequence of a DDoS attack. In mid-June, users the United States experienced problems accessing T-Mobile and Verizon networks. There were tweets about a large-scale DDoS attack on these wireless carriers and several social networks, allegedly originating in China, but these reports were left unconfirmed. On the contrary, T-Mobile stated that in reality, the affected resources, including those of the company’s competitors’, became inaccessible due to a wired provider failure in the Southeast, which caused network overload.
As failures and threat actors knocked out useful services, Dutch police shut down fifteen websites that sold DDoS attack services. In addition to that, in April Dutch law enforcement officers arrested a nineteen-year-old who attempted to disrupt the operation of several government portals in March. Police was determined to fight against services and individuals linked to DDoS activity. They have declared an intention to complicate this sort of attacks as much as they can.
Other countries have continued to fight DDoS attacks, too. In Israel, for example, former co-owners of a website that sold attack services were sentenced to six months of community service and fines. The malware service vDOS lasted four years and was shut down in 2016.
Quarter trends
Over the past few years, we have seen a significant drop in the number of DDoS attacks in the second quarter compared to the first, which is usually a tense period. However, from April to June of 2020, the picture remained nearly the same as in the previous reporting period: the overall number of attacks increased slightly, the number of smart attacks decreased slightly, but the profiles for the two quarters hardly differed overall.
Comparative number of DDoS attacks, Q1 and Q2 2020, and Q2 2019. Q2 2019 data taken as 100% (download)
The fact that the data we obtained for the “low” second quarter was virtually identical to that for the “high” first quarter is a testament to unprecedented growth in attacks in the reporting period. This is easy to see if one compares the figures for the second quarter of 2020 with the data for the same period in 2019: the total number of attacks more than tripled, and the number of smart attacks more than doubled.
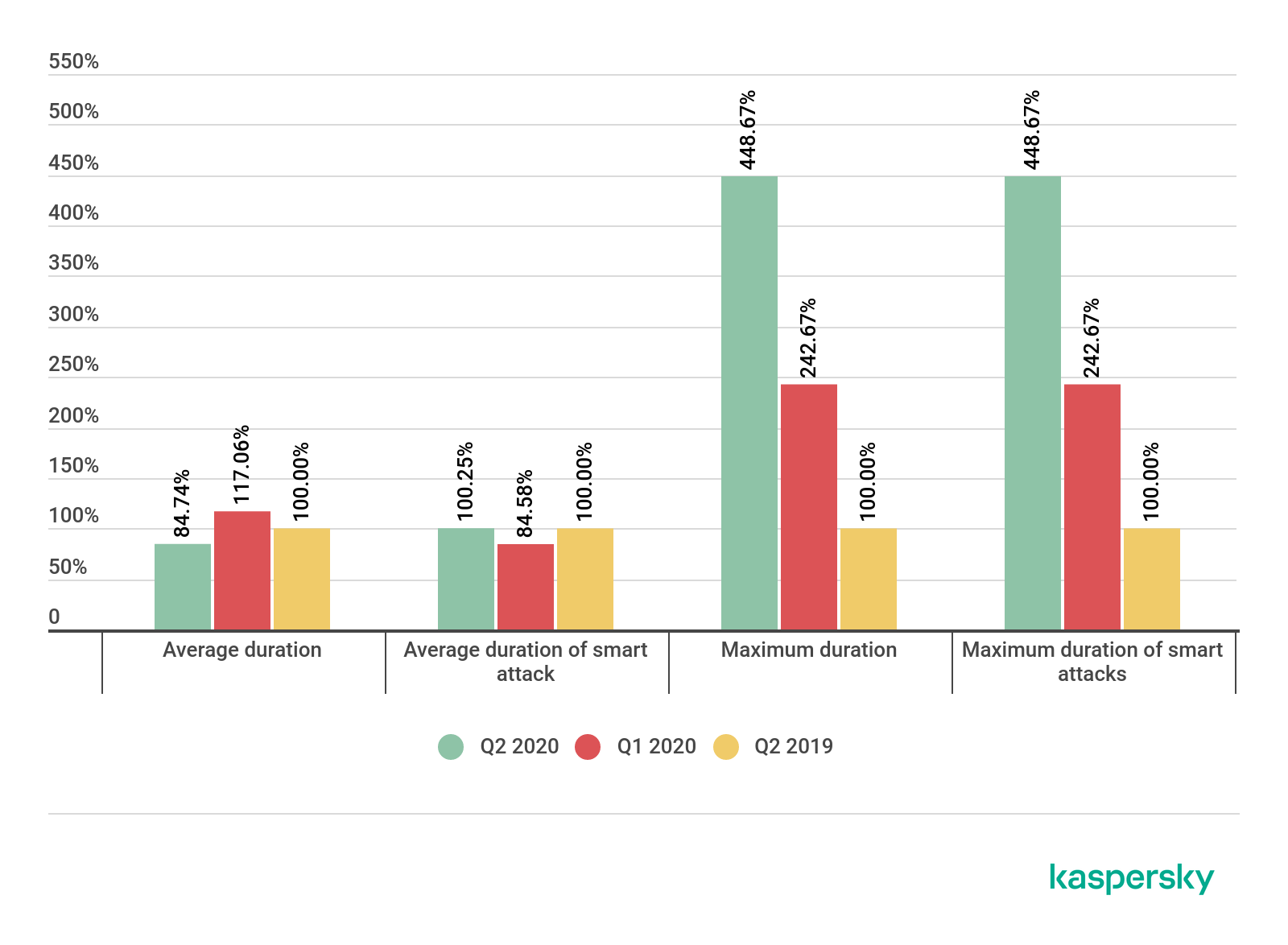
The duration of attacks on the average did not change in comparison with the first quarter or with last year, remaining at the level of around twenty minutes. Smart attacks, which lasted an average of several hours, were the longest. This trend has persisted for a long time, so this was nothing new to us. However, we should note that we observed an unusually long smart attack activity in the second quarter. This affected the maximum DDoS duration, which increased 4.5 times compared to last year. We excluded that attack from the sample when calculating averages.
Duration of DDoS attacks, the Q1 and Q2 2020, and Q2 2019 Q2 2019 data taken as 100% (download)
Just like the previous reporting period, the second quarter saw educational and government institutions targeted the most frequently. At the same time, the number of attacks on the educational sector decreased sharply starting in the second half of June, which could be attributed to the start of the summer break.
Quarter statistics
Quarter results
- The top three of the most attacked countries are the same: China (65.12%), the United States (20.28%) and Hong Kong, China (6.08%).
- Romania dropped out of the top ten and was ranked the 17th, whereas Great Britain rose from the eighteenth to the tenth position.
- The top five places in terms of both the number of targets and the number of attacks are occupied by China (66.02%), the United States (19.32%), Hong Kong, China (6.34%), South Africa (1.63%) and Singapore (1.04%).
- We are seeing the now-familiar trend of attacks abating begin to reverse: this April, their number grew, peaking at 298 on April 9.
- In the second quarter, we observed two dips several days long each, April 30 to May 6 and June 10–12, when the number of attacks remained within the range of ten to fifteen per day.
- DDoS botnet activity increased on Wednesdays and Thursdays and decreased on Saturdays.
- Even the longest attacks did not reach nine days (215, 214 and 210 hours), which is more than half the number of the previous quarter’s longest-lasting attacks (about 19 days).
- SYN flood remains the main DDoS attack tool (94.7%), ICMP attacks accounted for 4.9 percent, and other types of DDoS attacks were sidelined.
- The ratio of Windows-to-Linux botnets remained virtually unchanged, with the latter still responsible for the absolute majority (94.78%) of attacks.
Attack geography
In the second quarter of 2020, China (65.12%) again led by a wide margin, followed, as before, by the United States (20.28%) and Hong Kong, China (6.08%). The share of the first two countries increased by 3.59 and 1.2 p.p., respectively, whereas the share of Hong Kong, China decreased slightly, by 1.26 p.p.
Changes in the top ten were few as well. We are still seeing there South Africa (1.28%) Singapore (1.14%), both countries rising by a notch, now occupying the fourth and fifth positions, respectively. Next up is India (0.33%) and Australia (0.38%), which rose from ninth to seventh and from tenth to sixth place, respectively. These are followed by Canada (0.24%), which slipped to the ninth row.
Great Britain (0.18%; rose by 0.1 p.p.) is the newcomer in the rankings, sharing tenth place with South Korea. The EU countries, seldom targeted individually by DDoS operators, were seventh, with a share of 0.26%. Romania, however, slid from fourth to seventeenth place, dropping out of the top ten.
Distribution of DDoS attacks by country, Q1 and Q2 2020 (download)
The geographical distribution of unique targets traditionally replicates the distribution of attacks to a large extent. Six out of ten countries in the rankings overlap in the second quarter, with the top five being complete matches: China (66.02%), the United States (19.32%), Hong Kong, China (6.34%), South Africa (1.63%) and Singapore (1.04%). At the same time, only China registered an increase in the share of targets compared to the previous reporting period, by 13.31 p.p., while the rest showed a slight decline.
Sixth place went to Australia (0.3%), which was ninth in the first quarter. In addition, Vietnam returned to the top ten after a brief absence: with a small increase in the share of targets on its territory (just 0.06 p.p., to 0.23%), it occupied seventh position, displacing South Korea, which now shares the last two rows in the rankings with this quarter’s newcomer, Japan (0.18%), and has overtaken India, whose 0.23% of targets ensured that it took eighth place.
Distribution of unique DDoS attack targets by country, Q1 and Q2 2020 (download)
Dynamics of the number of DDoS attacks
The second quarter is normally calmer than the first, but this year is an exception. The long-term downward trend in attacks has unfortunately been interrupted, and this time we are witnessing an increase. The peaks occurred on April 9 (298 attacks) and April 1 (287 attacks within one day). Besides, the number of attacks exceeded the peak for the past two quarters twice, on May 13 and 16. In early May, DDoS operators apparently decided to go on a break: not once did the number of attacks reach fifteen within a day between April 30 and May 6, and between May 2 and May 4, just eight or nine per day were registered. The period of June 10–12 saw another lull, with 13, 15 and 13 attacks respectively.
The last three quarters have thus seen both a record high and a record low number of attacks. It is worth noting here that the quietest days repeated the absolute record in the observation period, set in the last quarter of 2019, but the busiest ones fall far short of even the relatively quiet third quarter. That said, the average number of attacks increased by almost thirty percent compared to the previous reporting period.
Dynamics of the number of DDoS attacks in Q2 2020 (download)
In the second quarter, the operators of the attacks preferred to work on Wednesdays (16.53%) and rested from their wicked deeds on Saturdays (only 11.65%). However, the difference between the “leader” and “anti-leader” is small, just 4.88 p.p. Compared to the last quarter, the share of attacks increased significantly on Wednesdays (by 5.37 p.p.) and Thursdays (by 3.22 p.p.), while Monday dropped (minus 3.14 p.p.).
Distribution of DDoS attacks by day of the week, Q1 and Q2 2020 (download)
Duration and types of DDoS attacks
The average duration of attacks decreased slightly (by 4 p.p.) when compared to the previous reporting period due to an increase in the share of ultrashort attacks and a decrease of 0.1 p.p. in the share of multi-day attacks, but more so due to an absence of ultra-long attacks. Whereas the first quarter saw attacks that lasted up to twenty days, this time, the top three lasted 215, 214 and 210 hours, that is less than nine days.
The distribution of attacks by duration has hardly changed: the aforementioned increase by 4 p.p. is the most significant event, with the remaining differences being within the range of 0.06 to 1.9 p.p., almost a statistical blip. Thus, the shortest attacks (up to four hours) accounted for 85.97% of the total number of DDoS attacks, those lasting five to nine hours for 8.87%, attacks up to 19 hours for 3.46%, attacks up to 49 hours for 1.39%, and attacks up to 99 hours in duration, for 0.11%. Attacks within the range of 100 to 139 hours proved to be slightly more numerous (0.16%), and the longest attacks accounted for 0.05% of the total DDoS attack number.
Distribution of DDoS attacks by duration (hours), Q1 and Q2 2020 (download)
The share of SYN flooding in the quarter was 94.7% (up by 2.1 p.p.). For a second consecutive quarter, the leader is followed by ICMP flooding (4.9%), which is 1.3 p.p. above the previous reporting period. TCP attacks accounted for 0.2% of the total number, and UDP and HTTP attacks (0.1%) round out the list. The share of the last three groups dropped when compared to the previous quarter.
Distribution of DDoS attacks by type, Q2 2020 (download)
The share of Windows botnets decreased by 0.41 p.p. to 5.22% compared to the previous quarter. Linux botnets thus account for 94.78% of all zombie networks.
Ratio of Windows and Linux botnet attacks, Q1 and Q2 2020 (download)
Conclusion
The second quarter of 2020 is notable for the number of DDoS attacks: the period from April through June normally sees a lull, but this year, DDoS activity increased in comparison to the previous reporting period. This is most likely due to the coronavirus pandemic and restrictive measures that lasted for part or all of the quarter in many countries. The forced migration of many day-to-day activities online led to an increase in potential DDoS targets. Little changed in the second quarter otherwise: the composition of the top ten list in terms of the number of attacks and targets was virtually the same, as was the distribution of attacks by duration. The proportion of all types of DDoS attacks, except for SYN and ICMP flood, dropped markedly, but talking about any kind of trend in this regard would be premature.
We expect third-quarter results, typically low, to be at about the same level as the second quarter, or to decrease slightly, having no reasons to believe otherwise at the time of writing this. It will be exceptionally interesting to watch attacks in the fourth quarter: the end of the year and the holiday season traditionally see no shortage of DDoS attacks, so if the trend continues — especially if we are hit by a second wave of the epidemic — it is possible that the DDoS market will grow significantly.


























DDoS attacks in Q2 2020