
Recently, we’ve found malicious code in version 3.17.18 of the official client of the APKPure app store. The app is not on Google Play, but it is itself a quite a popular app store around the world. Most likely, its infection is a repeat of the CamScanner incident, when the developer implemented a new adware SDK from an unverified source.
We notified the developers about the infection on April 8. APKPure confirmed the issue and promptly fixed it with the release of version 3.17.19.
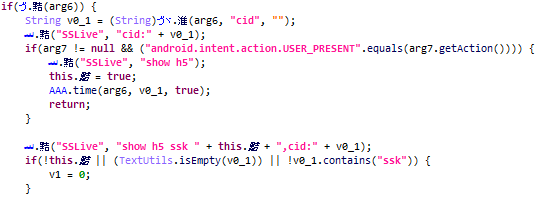
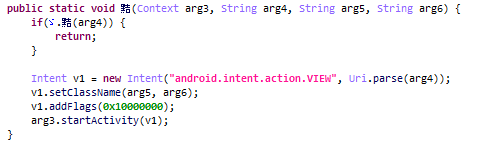
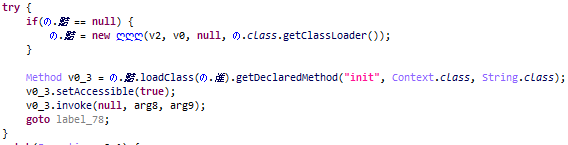
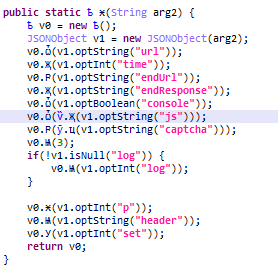
In terms of functionality, the malicious code embedded in APKPure is standard for this type of threat. When the app starts, the payload is decrypted and launched. In this case, it is located in a long string in the app code.

The payload collects information about the user device and sends it to the C&C server.
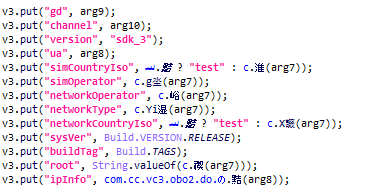
Next, depending on the response received, the malware can:
-
- Show ads when the device is unlocked.
-
- Open browser pages with ads repeatedly.
-
- Load additional executable modules.
In our case, a Trojan was loaded that has much in common with the notorious Triada malware and can perform a range of actions: from displaying and clicking ads to signing up for paid subscriptions and downloading other malware.
Depending on the OS version, the Trojan can inflict various forms of damage on the victim. APKPure users with current Android versions mostly risk having paid subscriptions and intrusive ads appear from nowhere. Users of smartphones who do not receive security updates are less fortunate: in outdated versions of the OS, the malware is capable of not only loading additional apps, but installing them on the system partition. This can result in an unremovable Trojan like xHelper getting onto the device.
Kaspersky solutions detect the malicious implant as HEUR:Trojan-Dropper.AndroidOS.Triada.ap.
If you use APKPure, we recommend immediately deleting the infected app and installing the “clean” 3.17.19 version. In addition, scan the system for other Trojans using a reliable security solution, such as Kaspersky Internet Security for Android.
IOCs
APKPure app
2cfaedcf879c62f5a50b42cbb0a7a499
718aecd85e9f1219f3fc05ef156d3acf
ceac990b3df466c0d23e0b7f588d1407
deac06ab75be80339c034e266dddbc9f
f64d43c64b8a39313409db2c846b3ee9
Payload
31e49ac1902b415e6716bc3fb048f381
Downloaded malware
5f9085a5e5e17cb1f6e387a901e765cf
C&C
https://wcf.seven1029[.]com
http://foodin[.]site/UploadFiles/20210406052812.apk
Malicious code in APKPure app






















DaoTrongChuong
I thank you for the article. But may I ask what applications did you use to analyze their malware. And I also know about Ghidra software and how is it different from IDA PRO . I sincerely thank you.
No
Is this still relevant with the current version?
Securelist
Hi No!
No, APKPure fixed the issue with the release of version 3.17.19 soon after it was discovered.