
These statistics are based on detection verdicts of Kaspersky products received from users who consented to providing statistical data.
Figures of the year
In 2022, Kaspersky mobile products and technology detected:
- 1,661,743 malicious installers
- 196,476 new mobile banking Trojans
- 10,543 new mobile ransomware Trojans
Trends of the year
Mobile attacks leveled off after decreasing in the second half of 2021 and remained around the same level throughout 2022.
Kaspersky mobile cyberthreat detection dynamics in 2020–2022 (download)
Cybercriminals continued to use legitimate channels to spread malware.
Similarly to 2021, we found a modified WhatsApp build with malicious code inside in 2022. It was notable for spreading via ads inside the popular Snaptube app and through the Vidmate in-app store.
The spread of malware through Google Play continued as well. In particular, we found several mobile Trojan subscribers on Google’s official Android app marketplace in 2022. These secretly signed users up for paid services. In addition to the previously known Jocker and MobOk families, we discovered a new family, named Harly and active since 2020. Harly malware programs were downloaded a total of 2.6 million times from Google Play in 2022. Also last year, fraudsters abused the marketplace to spread various scam apps, which promised welfare payments or lucrative energy investments.
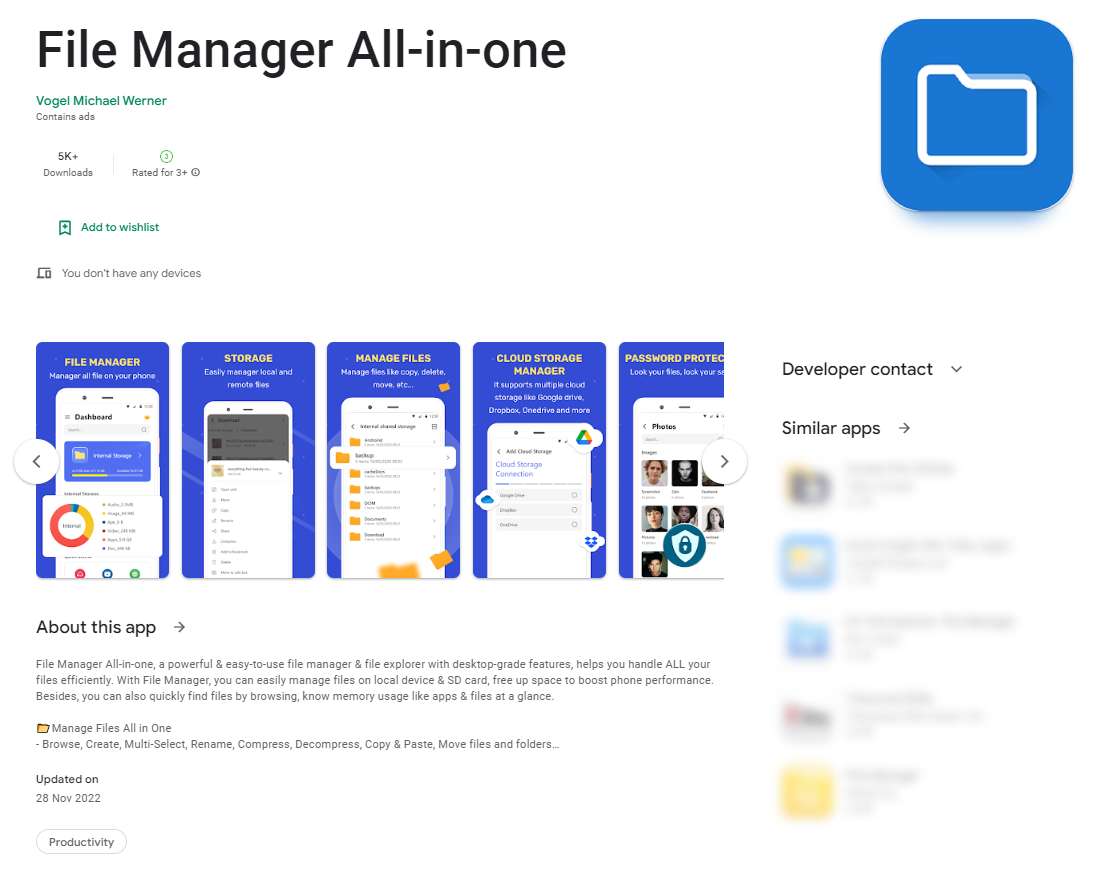
Mobile banking Trojans were not far behind. Despite Europol having shut down the servers of FluBot (also known as Polph or Cabassous, the largest mobile botnet in recent years), users had to stay on guard, as Google Play still contained downloaders for other banking Trojan families, such as Sharkbot, Anatsa/Teaban, Octo/Coper, and Xenomorph, all masquerading as utilities. For instance, the Sharkbot downloader in the screenshot below imitates a file manager. This type of software is capable of requesting permission to install further packages the Trojan needs to function on the unsuspecting user’s device.
The Sharkbot banking Trojan downloader on Google Play
Exploitation of popular game titles, where malware and unwanted software mimicked a pirated version of a game or game cheats, remained a popular mobile spread vector in 2022. The most frequently imitated titles included Minecraft, Roblox, Grand Theft Auto, PUBG, and FIFA. The malware spread primarily through questionable web sites, social media groups, and other unofficial channels.
Mobile cyberthreat statistics
Installer numbers
We detected 1,661,743 malware or unwanted software installers in 2022 — 1,803,013 less than we did in 2021. The number had been declining gradually since a 2020 increase.
Number of detected malicious installation packages in 2019–2022 (download)
Distribution of detected mobile malware by type
Distribution of newly detected mobile malware by type in 2021 and 2022 (download)
RiskTool-type potentially unwanted software (27.39%) topped the rankings in 2022, replacing the previous leader, adware (24.05%). That said, the share of RiskTool had decreased by 7.89 percentage points, and the share of adware, by 18.38 percentage points year-on-year.
Various Trojan-type malware was third in the rankings with 15.56%, its cumulative share increasing by 6.7 percentage points.
Geography of mobile threats
TOP 10 countries by share of users attacked by mobile malware
| Country* | %** | |
| 1 | China | 17.70 |
| 2 | Syria | 15.61 |
| 3 | Iran | 14.53 |
| 4 | Yemen | 14.39 |
| 5 | Iraq | 8.44 |
| 6 | Saudi Arabia | 6.78 |
| 7 | Kenya | 5.52 |
| 8 | Switzerland | 5.44 |
| 9 | Pakistan | 5.21 |
| 10 | Tanzania | 5.15 |
* Excluded from the rankings are countries with relatively few users of Kaspersky mobile security (under 10,000).
** Unique users attacked as a percentage of all Kaspersky mobile security users in the country.
China had the largest share of users who experienced a mobile malware attack: 17.70%. Of these, 16.06% got hit by SMS-abusing malware that we detected as Trojan.AndroidOS.Najin.a.
Other countries with significant shares of attacked users were Syria (15.61%) and Iran (14.53%), where the most frequently encountered mobile cyberthreat was Trojan-Spy.AndroidOS.Agent.aas, a WhatsApp modification carrying a spy module.
Distribution of attacks by type of software used
Distribution of attacks by type of software used in 2022 (download)
Similarly to previous years, 2022 saw malware used in most mobile attacks (67.78%). The shares of attacks that used Adware- and RiskWare-type applications had increased to 26.91% from 16.92% in 2021 and to 5.31% from 2.38% in 2021, respectively.
Mobile adware
The Adlo family accounted for the largest share of detected installers (22.07%) in 2022. These are useless fake apps that download ads. Adlo replaced the previous leader, the Ewind family, which had a share of 16.46%.
TOP 10 most frequently detected adware families in 2022
| Family | %* | |
| 1 | Adlo | 22.07 |
| 2 | Ewind | 16.46 |
| 3 | HiddenAd | 15.02 |
| 4 | MobiDash | 11.30 |
| 5 | Dnotua | 5.08 |
| 6 | FakeAdBlocker | 5.02 |
| 7 | Agent | 4.02 |
| 8 | Fyben | 3.94 |
| 9 | Notifyer | 3.19 |
| 10 | Dowgin | 1.38 |
* The share of the adware-type family in the total number of adware installers detected.
RiskTool-type apps
The SMSreg family retained its lead by number of detected RiskTool-type apps: 36.47%. The applications in this family make payments (for example by transferring cash to other individuals or paying for mobile service subscriptions) by sending text messages without explicitly notifying the user.
TOP 10 most frequently detected RiskTool families, 2022
| Family | %* | |
| 1 | SMSreg | 36.47 |
| 2 | Dnotua | 26.19 |
| 3 | Robtes | 24.41 |
| 4 | Resharer | 2.67 |
| 5 | Agent | 2.39 |
| 6 | SmsSend | 1.29 |
| 7 | SpyLoan | 1.29 |
| 8 | Skymobi | 1.10 |
| 9 | SmsPay | 0.71 |
| 10 | Wapron | 0.66 |
* The share of the RiskTool family in the total number of RiskTool installers detected.
TOP 20 most frequently detected mobile malware programs
Note that the malware rankings below exclude riskware or potentially unwanted software, such as RiskTool or adware.
| Verdict | %* | |
| 1 | DangerousObject.Multi.Generic | 18.97 |
| 2 | Trojan-SMS.AndroidOS.Fakeapp.d | 8.65 |
| 3 | Trojan.AndroidOS.Generic | 6.70 |
| 4 | Trojan-Spy.AndroidOS.Agent.aas | 6.01 |
| 5 | Trojan.AndroidOS.Fakemoney.d | 4.65 |
| 6 | Trojan.AndroidOS.GriftHorse.l | 4.32 |
| 7 | Trojan-Dropper.AndroidOS.Agent.sl | 3.22 |
| 8 | DangerousObject.AndroidOS.GenericML | 2.96 |
| 9 | Trojan-SMS.AndroidOS.Fakeapp.c | 2.37 |
| 10 | Trojan.AndroidOS.Fakeapp.ed | 2.19 |
| 11 | Trojan.AndroidOS.GriftHorse.ah | 2.00 |
| 12 | Trojan-Downloader.AndroidOS.Agent.kx | 1.72 |
| 13 | Trojan.AndroidOS.Soceng.f | 1.67 |
| 14 | Trojan-Dropper.AndroidOS.Hqwar.hd | 1.49 |
| 15 | Trojan.AndroidOS.Fakeapp.dw | 1.43 |
| 16 | Trojan-Ransom.AndroidOS.Pigetrl.a | 1.43 |
| 17 | Trojan-Downloader.AndroidOS.Necro.d | 1.40 |
| 18 | Trojan-SMS.AndroidOS.Agent.ado | 1.36 |
| 19 | Trojan-Dropper.AndroidOS.Hqwar.gen | 1.35 |
| 20 | Trojan-Spy.AndroidOS.Agent.acq | 1.34 |
* Unique users attacked by the malware as a percentage of all attacked Kaspersky mobile security users.
First and third places went to DangerousObject.Multi.Generic (18.97%) and Trojan.AndroidOS.Generic (6.70%), respectively, which are verdicts we use for malware detected with cloud technology. Cloud technology is triggered whenever the antivirus databases lack data for detecting a piece of malware, but the antivirus company’s cloud already contains information about the object. This is essentially how the latest malware types are detected.
The Trojans in second and ninth places (8.65% and 2.37%) belonged to the Trojan-SMS.AndroidOS.Fakeapp family. This type of malware is capable of sending text messages and calling preset numbers, displaying ads, and hiding its icon on the device.
WhatsApp modifications equipped with a spy module, detected as Trojan-Spy.AndroidOS.Agent.aas (6.01%) and Trojan-Spy.AndroidOS.Agent.acq (1.34%) were in fourth and twentieth positions, respectively.
Scam apps detected as Trojan.AndroidOS.Fakemoney.d (4.65%) were the fifth-largest category. These try to trick users into believing that they are filling out an application for a welfare payout.
Members of the Trojan.AndroidOS.GriftHorse family, which subscribe the user to premium SMS services, took both sixth and eleventh places (4.32% and 2%, respectively).
The banking Trojan dropper Trojan-Dropper.AndroidOS.Agent.sl (3.22%) was seventh.
The verdict of DangerousObject.AndroidOS.GenericML (2.96%) sank to eighth place. The verdict is assigned to files recognized as malicious by our machine-learning systems.
Tenth place was taken by Trojan.AndroidOS.Fakeapp.ed (2.19%). This verdict refers to a category of fraudulent apps which target users in Russia by posing as a stock-trading platform for investing in gas.
Trojan-Downloader.AndroidOS.Agent.kx (1.72%) rose to twelfth position. This type of malware is distributed as part of legitimate software, downloading advertising modules.
Trojan.AndroidOS.Soceng.f (1.67%), in thirteenth place, sends text messages to people on your contact list, deletes files on the SD card, and overlays the interfaces of popular apps with its own window.
Malware from the Trojan-Dropper.AndroidOS.Hqwar family, which unpacks and runs various banking Trojans, occupied fourteenth and nineteenth places (1.49 and 1.35%).
Trojan.AndroidOS.Fakeapp.dw was fifteenth (1.43%). The verdict applies to a variety of scam apps, such as those supposedly offering the user to earn some extra cash.
Trojan-Ransom.AndroidOS.Pigetrl.a (1.43%) took sixteenth place. Unlike classic Trojan-Ransom malware, which typically demands a ransom, it simply locks the screen and asks to enter a code. The application offers no instructions on obtaining the code, which is embedded in the program itself.
Trojan-Downloader.AndroidOS.Necro.d sank to seventeenth position (1.4%). This malware is capable of downloading, installing, and running other applications when commanded by its operators.
Trojan-SMS.AndroidOS.Agent.ado, which sends text messages to shortcodes, was eighteenth (1.36%).
Mobile banking Trojans
We detected 196,476 mobile banking Trojan installers in 2022, a year-on-year increase of 100% and the highest figure in the past six years.
The Trojan-Banker.AndroidOS.Bray family accounted for two-thirds (66.40%) of all detected banking Trojans. This family attacked mostly users in Japan. It was followed by the Trojan-Banker.AndroidOS.Fakecalls family (8.27%) and Trojan-Banker.AndroidOS.Bian (3.25%).
The number of mobile banking Trojan installers detected by Kaspersky in 2019–2022 (download)
Although the number of detected malware installers rose in 2022, mobile banking Trojan attacks had been decreasing since a 2020 rise.
The number of mobile banking Trojan attacks in 2021–2022 (download)
TOP 10 most frequently detected mobile banking Trojans
| Verdict | %* | |
| 1 | Trojan-Banker.AndroidOS.Bian.h | 28.74 |
| 2 | Trojan-Banker.AndroidOS.Anubis.t | 11.50 |
| 3 | Trojan-Banker.AndroidOS.Svpeng.q | 5.50 |
| 4 | Trojan-Banker.AndroidOS.Agent.ep | 5.25 |
| 5 | Trojan-Banker.AndroidOS.Agent.eq | 4.51 |
| 6 | Trojan-Banker.AndroidOS.Gustuff.d | 3.88 |
| 7 | Trojan-Banker.AndroidOS.Asacub.ce | 3.54 |
| 8 | Trojan-Banker.AndroidOS.Sova.g | 2.72 |
| 9 | Trojan-Banker.AndroidOS.Faketoken.z | 2.01 |
| 10 | rojan-Banker.AndroidOS.Bray.f | 1.71 |
* Unique users attacked by this malware as a percentage of all Kaspersky mobile security users attacked by banking threats.
Of all mobile banking Trojans that were active in 2022, Trojan-Banker.AndroidOS.Bian.h (28.74%) accounted for the largest share of attacked users, more than half of those in Spain.
TOP 10 countries by share of users attacked by mobile banking Trojans
| Country* | %** | |
| 1 | Spain | 1.96 |
| 2 | Saudi Arabia | 1.11 |
| 3 | Australia | 1.09 |
| 4 | Turkey | 0.99 |
| 5 | China | 0.73 |
| 6 | Switzerland | 0.48 |
| 7 | Japan | 0.30 |
| 8 | Colombia | 0.19 |
| 9 | Italy | 0.17 |
| 10 | India | 0.16 |
* Excluded from the rankings are countries with relatively few users of Kaspersky mobile security (under 10,000).
** Unique users attacked by mobile banking Trojans as a percentage of all Kaspersky mobile security users in the country.
Spain had the largest share of unique users attacked by mobile financial threats in 2022 (1.96%), with 85.90% of the affected users encountering the aforementioned Trojan-Banker.AndroidOS.Bian.h.
It was followed by Saudi Arabia (1,11%), also due to Trojan-Banker.AndroidOS.Bian.h, which affected 97.92% of users in that country.
Australia (1.09%) was third, with 98% of the users who encountered banking Trojans there attacked by Trojan-Banker.AndroidOS.Gustuff.
Mobile ransomware Trojans
We detected 10,543 mobile ransomware Trojan installers in 2022, which was 6,829 less than the 2021 figure.
The number of mobile ransomware Trojan installers detected by Kaspersky in 2019–2022 (download)
The number of mobile ransomware Trojan attacks also continued to decline, a process that started in late 2021.
The number of mobile ransomware Trojan attacks in 2021–2022 (download)
| Verdict | %* | |
| 1 | Trojan-Ransom.AndroidOS.Pigetrl.a | 75.10 |
| 2 | Trojan-Ransom.AndroidOS.Rkor.br | 3.70 |
| 3 | Trojan-Ransom.AndroidOS.Small.as | 1.81 |
| 4 | Trojan-Ransom.AndroidOS.Rkor.bs | 1.60 |
| 5 | Trojan-Ransom.AndroidOS.Rkor.bi | 1.48 |
| 6 | Trojan-Ransom.AndroidOS.Rkor.bt | 1.19 |
| 7 | Trojan-Ransom.AndroidOS.Fusob.h | 1.05 |
| 8 | Trojan-Ransom.AndroidOS.Rkor.ch | 0.99 |
| 9 | Trojan-Ransom.AndroidOS.Rkor.bp | 0.92 |
| 10 | Trojan-Ransom.AndroidOS.Congur.cw | 0.90 |
* Unique users attacked by the malware as a percentage of all Kaspersky mobile security users attacked by ransomware Trojans.
Trojan-Ransom.AndroidOS.Pigetrl.a remained the leading ransomware Trojan family in 2022 (75.10%). It was also one of the TOP 20 most frequently detected mobile malware types. Russia accounted for as much as 92.74% of detections.
That malware family was followed by Trojan-Ransom.AndroidOS.Rkor, which blocks the screen and demands the user to pay a fine for some illegal content they had supposedly viewed. Members of this family took six out of ten places in our rankings, with as much as 65.27% attacked users located in Kazakhstan.
TOP 10 countries by share of users attacked by mobile ransomware Trojans
| Country* | %** | |
| 1 | China | 0.65 |
| 2 | Yemen | 0.49 |
| 3 | Kazakhstan | 0.36 |
| 4 | Iraq | 0.08 |
| 5 | Azerbaijan | 0.05 |
| 6 | Kyrgyzstan | 0.05 |
| 7 | Switzerland | 0.04 |
| 8 | Saudi Arabia | 0.04 |
| 9 | Lebanon | 0.04 |
| 10 | Egypt | 0.03 |
* Excluded from the rankings are countries with relatively few Kaspersky mobile security users (under 10,000).
** Unique users attacked by mobile ransomware Trojans as a percentage of all Kaspersky mobile security users in the country.
We observed the highest shares of users attacked by mobile ransomware Trojans in 2022 in China (0.65%), Yemen (0.49%), and Kazakhstan (0.36%).
Users in China mostly encountered Trojan-Ransom.AndroidOS.Congur.y, most users in Yemen were affected by Trojan-Ransom.AndroidOS.Pigetrl.a, and a majority of users in Kazakhstan were hit by Trojan-Ransom.AndroidOS.Rkor.br.
Conclusion
The cybercriminal activity leveled off in 2022, with attack numbers remaining steady after a decrease in 2021. That said, cybercriminals are still working on improving both malware functionality and spread vectors. Malware is increasingly spreading through legitimate channels, such as official marketplaces and ads in popular apps. This is true for both scam apps and dangerous mobile banking malware.
Potentially unwanted applications (RiskWare) accounted for a majority of newly detected threats in 2022, replacing the previous leader, adware. Most mobile cyberattacks used malware as before.
The mobile malware threat landscape in 2022

















Anuugya sarraswat
Nice research, what are the data sources? It includes 3rd party products also or data via
Kaspersky Only?
Securelist
Hi Anuugya!
The statistics are based on detection verdicts of Kaspersky products received from users who consented to providing statistical data.
Mahhn
Just added a note to say, great write up. If you had a thumbs up button, I would be clicking it on most of the stories.